The Active Directory integration works when the Personify360 application server is a member of the domain it is authenticating against (the user’s AD domain). This poses a challenge for managed services staff to be able to administer the server, because they have to have credentials and rights in the foreign domain. Therefore, the Lightweight Directory Access Protocol (LDAP) allows user to authenticate the user against their domain controller.
Administrators can configure LDAP in the Personify.Server.ApplicationServer.exe.config file under PersonifySettings:

Attribute |
Description |
|---|---|
Domain |
Name of the Active Directory Domain
Example: MYDOMAIN |
ServerName |
Name or IP Address of the user directory server.
Example: MyServer |
Port |
The port number where the user directory is running.
Example: 389 |
UseSecureLDAP |
When set to True, enables Secure Socket Layer (SSL) communication with the user directory. The user directory must be configured for secure communication. |
LDAPVersion |
Lightweight Directory Protocol Version
Example: 3 |
BaseDN |
The distinguished name (DN) of the node where the search for users should begin.
Example: dc=example,dc=com |
SearchFilter |
LDAP query filter used to retrieve directory users and shall include object classes and keyword.
Example: (&(objectClass=person)(|(cn=*{0}*)(sn=*{0}*)(givenname=*{0}*)(uid=*{0}*)(mail=*{0}*))) |
SearchSizeLimit |
Maximum number of results that a search can return. If this value is greater than that supported by the user directory settings, the user directory value overrides this value. Set the value to 0 to retrieve all users that meet the search criteria.
|
IDAttribute |
A unique user attribute.
Example: entryDN |
UseBasicAuth |
When set to True, uses basic authentication else uses Authorization Type Negotiate
|
IsActiveDirectory |
Flag to identify Active Directory or LDAP-based user directory
|
In order to use LDAP authentication, a System Administrator must disable the legacy Active Directory integration. When Active Directory is enabled, the Personify360 log in screen will display the Use Windows Authentication option and system administrators have the option to add a new network user in Personify360.
To disable active directory, set the EnableActiveDirectoryIntegration value to "False" in the config.xml, as shown below.
<Item Name="UserInterface"
SplashScreen="False"
ApplicationHostType="MDIMain"
StartupCommand="file://./HTMLPages\startscreen5.html"
ConfigFolder="Config"
DefaultRole="CallCenterRep"
AdvancedThemes="True"
DefaultTheme="TIMSS_Default.isl"
CustomerProfileURL="http://YourClientWebSite/CustomerProfile/Main.aspx"
RememberPassword="True"
RememberUserId="True"
EnableActiveDirectoryIntegration="False"
EnableLDAPIntegration="True"
ConstituentProfileURL="http://YourClientWebSite/ConstituentProfile/Main.aspx"
MailMergeDirectoryPath="C:\"
BroadcastingEnabled="False"
BroadcastingFrequency="30"
BroadcastMessageDisplayTimeout="15"
UnresolvedIssueAlertFrequencyInMinutes="5"
ReportTaskFormat="DESCRIPTION (CODE)"
EnableDatabaseFilter="False"
AutomaticCapitalization="True"
EnableAddModOperatorAlias="True"
/>When the LDAP integration is enabled, system administrators can add/modify a network user in Personify360 Operations.
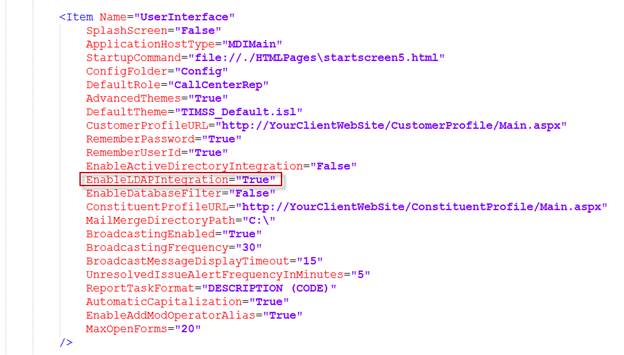
To enable LDAP authentication, set the EnableLDAPIntegration to "True" in the config.xml file, as shown below.
<Item Name="UserInterface"
SplashScreen="False"
ApplicationHostType="MDIMain"
StartupCommand="file://./HTMLPages\startscreen5.html"
ConfigFolder="Config"
DefaultRole="CallCenterRep"
AdvancedThemes="True"
DefaultTheme="TIMSS_Default.isl"
CustomerProfileURL="http://YourClientWebSite/CustomerProfile/Main.aspx"
RememberPassword="True"
RememberUserId="True"
EnableActiveDirectoryIntegration="False"
EnableLDAPIntegration="True"
ConstituentProfileURL="http://YourClientWebSite/ConstituentProfile/Main.aspx"
MailMergeDirectoryPath="C:\"
BroadcastingEnabled="False"
BroadcastingFrequency="30"
BroadcastMessageDisplayTimeout="15"
UnresolvedIssueAlertFrequencyInMinutes="5"
ReportTaskFormat="DESCRIPTION (CODE)"
EnableDatabaseFilter="False"
AutomaticCapitalization="True"
EnableAddModOperatorAlias="True"
/> Both
EnableLDAPIntegration and EnableActiveDirectoryIntegration
options should never be set to "TRUE". The logic for authentication
is: If EnableLDAPIntegration =
TRUE, use LDAP authentication. Else if EnableActiveDirectoryIntegration
= TRUE, use Active Directory authentication. Else, use Personify360 authentication.
Both
EnableLDAPIntegration and EnableActiveDirectoryIntegration
options should never be set to "TRUE". The logic for authentication
is: If EnableLDAPIntegration =
TRUE, use LDAP authentication. Else if EnableActiveDirectoryIntegration
= TRUE, use Active Directory authentication. Else, use Personify360 authentication.